In today’s interconnected world, collaboration has become a key driver of success. At 4PSA we know—strong teamwork culture is not just a buzzword. It is a vital aspect of modern organizations that want to thrive and excel.

In today’s interconnected world, collaboration has become a key driver of success. At 4PSA we know—strong teamwork culture is not just a buzzword. It is a vital aspect of modern organizations that want to thrive and excel.

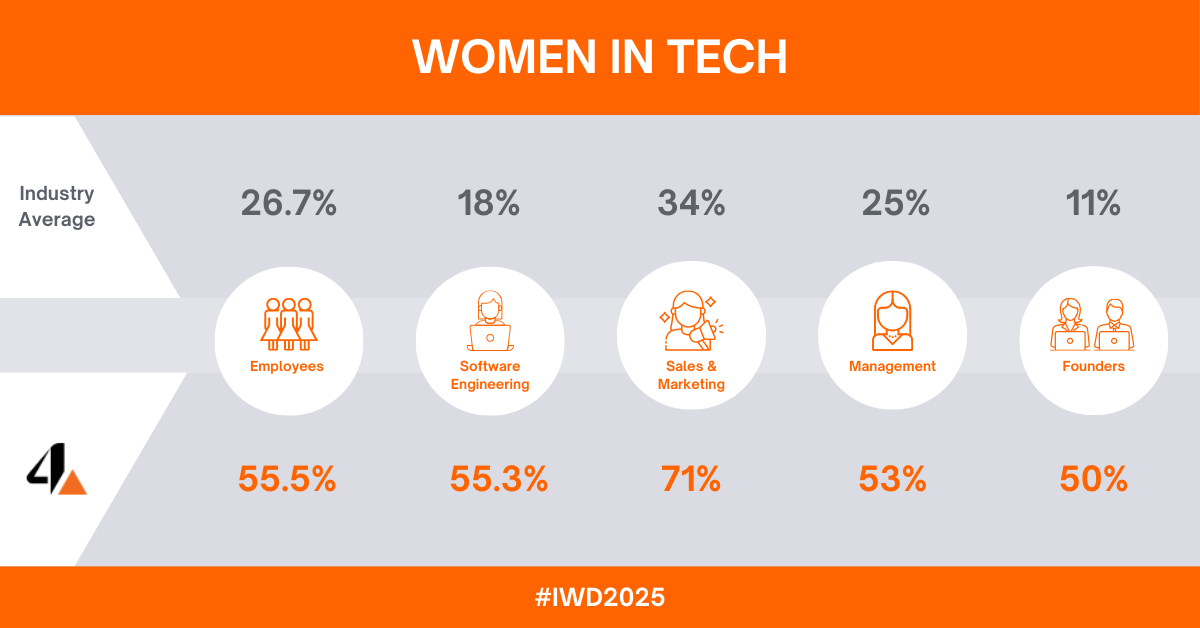
International Women’s Day (IWD), observed annually on March 8, serves as a global rally for gender equality, a mission that resonates profoundly within the technology sector. As we mark this day in 2025, we reflect not only on the advancements made by women in tech but also on the systemic barriers that persist. The underrepresentation of women in tech roles—a gap that stifles innovation and economic growth—remains a critical challenge.
In today’s digital age, communication has undergone a remarkable transformation. One of the key technologies driving this change is IP telephony, also referred to as internet telephony or Voice over IP (VoIP). This innovative approach allows voice and multimedia sessions to be transmitted over the internet, providing a more efficient, cost-effective, and versatile alternative to traditional telephone systems.

When it comes to managing your time at work, you’re often trapped in a relentless loop of ticking off daily tasks. Yet, shifting focus toward goal oriented performance rather than mere checklists can unlock substantial progress and align efforts with what genuinely drives long-term success.

In the world of business communication, call parking is a concept that plays a crucial role in ensuring efficient and effective handling of phone calls. By temporarily parking a call, businesses can easily transfer and retrieve calls between different extensions without disrupting the flow of communication.

In the dynamic world of JavaScript, coding conventions and rules are essential for maintaining code readability, consistency, and collaboration within teams. Using coding standards streamlines debugging and reduces errors. For beginners and students, understanding these standards is crucial, as it ensures that code is not only functional, but also clean and easy to comprehend for others.

Unified Communications as a Service (UCaaS) handles all communications and collaboration tools in one place. It can cover everything from telephony, internal communication, to customer service and even employee onboarding. Hence its importance because the ultimate goal is for your business customers is to have communications systems that allow them to grow and scale.

January can be a tough month, especially after the excitement and joy of December. The post-holiday winter blues is real, and it’s common to feel sluggish, unmotivated, and disconnected from your goals. But it’s exactly this time of year that you need to refocus and get back on track.

In today’s increasingly intricate digital landscape, maintaining cyber resilience is more crucial than ever. This involves not only proactively safeguarding against threats but also ensuring a swift recovery in the event of a breach. As organizations and individuals continue to rely on digital technologies, robust cybersecurity measures are essential to preventing disruptions and mitigating potential losses. One of the most powerful tools in the fight against cyber threats is multi factor authentication. MFA is a highly effective strategy for strengthening cyber resilience. Let’s delve deeper and explore its optimal implementation scenarios.

Clear customer communication is a cornerstone of business success. When companies communicate effectively, both internally and externally, they can set realistic expectations, deliver exceptional customer service, and appeal to prospective leads. This approach not only enhances the customer experience but also builds trust and loyalty, which are vital for long-term growth.
